Summary and opinions on President Biden’s Executive Order (EO) 14028
Table of contents
- Introduction
- Summary
- Section 1. Policy
- Section 2. Removing Barriers to Sharing Threat Information – Summary
- Section 3. Modernizing Federal Government Cybersecurity – Summary
- Zero Trust Architecture (ZTA)
- Movement to secure cloud services
- Section 4. Enhancing Software Supply Chain Security – Summary
- Section 5. Establishing a Cyber Safety Review Board – Summary
- Section 6. Standardizing the Federal Government’s Playbook for Responding to Cybersecurity Vulnerabilities and Incidents – Summary
- Section 7. Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal Government Networks – Summary
- Section 8. Improving the Federal Government’s Investigative and Remediation Capabilities – Summary
- Section 9. National Security Systems – Summary
- Section 10. Definitions – Summary
- Section 11. General Provisions – Summary
- Conclusion
Introduction
On May 12, 2021, President Biden issued Executive Order (EO) 14028. The EO was published into the Federal Register on May 17, 2021 and can be referenced online here:
https://www.federalregister.gov/documents/2021/05/17/2021-10460/improving-the-nationscybersecurity
This document is a summary interpretation of the EO and our unbiased opinion, section by section.
Summary
There are eleven sections in the EO, each with a subset of topics, deadlines, and responsible parties:
- Section 1. Policy
- Section 2. Removing Barriers to Sharing Threat Information
- Section 3. Modernizing Federal Government Cybersecurity
- Section 4. Enhancing Software Supply Chain Security
- Section 5. Establishing a Cyber Safety Review Board
- Section 6. Standardizing the Federal Government’s Playbook for Responding to Cybersecurity
- Vulnerabilities and Incidents
- Section 7. Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal
- Government Networks
- Section 8. Improving the Federal Government’s Investigative and Remediation Capabilities
- Section 9. National Security Systems
- Section 10. Definitions
- Section 11. General Provisions
The titles are good indicators of each section’s contents; however, there are some interesting, and maybe concerning “hidden gems” found in the details. Zero Trust Architecture, Endpoint Detection and Response are specifically called out, and these could turn out disastrous if they’re not done right or if they’re done for the wrong reasons. Few would argue that the Federal Government doesn’t need to do a better job protecting its assets. This EO could be exactly what the country needs.
On the other hand, an EO with poorly written requirements and/or ulterior motives could be worse than no EO at all.
If you only read the titles of each section, you might be very supportive of this EO. If you read the details within each section, which we did, you might find some things you don’t feel completely comfortable with. We encourage everyone to read the President’s EO in detail and form your own opinions, then share them with us.
We promise to respect your opinions, and we hope you will reciprocate.
Section 1. Policy – Summary
A standard opening and the Biden Administration’s justification for the EO.
The policy statement is:
It is the policy of my Administration that the prevention, detection, assessment, and remediation of
cyber incidents is a top priority and essential to national and economic security.
The scope of the EO is:
All Federal Information Systems should meet or exceed the standards and requirements for
cybersecurity set forth in and issued pursuant to this order.
Section 1 also contains admissions that the Federal Government must improve “cybersecurity”, must partner with the private sector, must make “bold changes and significant investments”, and must “bring to bear the full scope of its authorities and resources”.
Section 1. Policy – Opinion
Section one sounds good. The right words are used in the right places, and the right justifications are used to support the EO.
There should be little doubt our country needs to do “cybersecurity” better, but we can’t help feeling some level of distrust based on track record and political motivations.
Information security is logical and should never be political.
Maybe our feelings are just run of the mill paranoia, or maybe our feelings are justified by witnessing our Federal Government operate with a less than stellar track record:
- There’s no objection to partnering with the private sector; however, the government has a reputation of only working with the powerful people in the private sector.
- There’s no objection to making “bold changes and significant investments”; however, the government has a reputation of making bold changes with ulterior motives and making HUGE investments on bad things.
- Anytime our Federal Government says it “must bring to bear the full scope of its authorities and resources” (or something similar), the hairs rise on the back of our collective necks and we cringe a little.
If the goal is to secure the government (and the country better), then let’s look at the rest of this EO with this lens. Let’s NOT look at this EO with a political or emotional lens.
Section 2. Removing Barriers to Sharing Threat Information – Summary
This section is mostly related to establishing better “cyber incident” reporting between contracted IT and OT service providers and the Federal Government.
Topics covered in this section include:
- Review existing reporting requirements and procedures.
- Recommend updates to the Federal Acquisition Regulation (FAR).
- Update the FAR.
- Enforce IT/OT provider compliance.
- Centralize reporting.
- Provide budget for this section.
The timelines are aggressive, and several deadlines are mentioned, the latest being October 9, 2021.
Section 2. Removing Barriers to Sharing Threat Information – Opinion
One of the best sections in the EO, setting proper expectations for incident information sharing. We’re very interested to see the specific requirements once they’ve been vetted and communicated. The requirements in this section should go a long way toward ensuring incident information is shared properly and promptly between concerned parties. A quick and coordinated response should significantly limit the impact of future incidents.
Section 3. Modernizing Federal Government Cybersecurity – Summary
The main purpose for this section is to force wider adoption of cloud technologies, a Zero Trust Architecture (ZTA), and multi-factor authentication (MFA).
According to this section, the Federal Government must:
- Adopt security best practices.
- Advance toward Zero Trust Architecture
- Accelerate movement to secure cloud services.
- Adopt multi-factor authentication.
- Encrypt data at rest and in transit.
- Centralize and streamline access to cybersecurity data.
- Invest in both technology and personnel to match the modernization goals.
The timelines for the requirements in this section are also aggressive, for instance, the plan to implement a Zero Trust Architecture is due within 60 days (7/11/21).
Section 3. Modernizing Federal Government Cybersecurity – Opinion
This is a weighty section with many requirements, and the timelines are VERY ambitious. On the surface, everything in this section seems good, until we consider reality.
Security best practices are good, adopting multi-factor authentication is good, encrypting data at rest and in transit seems good (although it could disrupt some things), and centralizing and streamlining access should be good depending upon the implementation.
To be blunt, pushing the Zero Trust Architecture (ZTA) on this scale seems premature. There are many steps that could be made towards ZTA without going all the way this quickly. Taking steps is doable and effective but pushing ZTA the way this EO does seems unrealistic and more marketing than substance. Many people in our industry see “ZTA” as marketing on what have always been seen as best practice.
Accelerating movement/migration to the cloud also gives us an uneasy feeling. Is the cloud more secure than on premise? Maybe, but that’s almost like saying Apple is more secure than Linux. It sort of depends, doesn’t it? One could make the argument that the cloud is not inherently more secure, so why are we accelerating the migration to the cloud on this scale? Feels more about money than security, but the EO doesn’t give all the justification either.
Zero Trust Architecture (ZTA)
ZTA is generally good and conceptually sound. Despite all the marketing BS by vendors trying to make a buck (at our expense), ZTA draws upon information security concepts we’ve been preaching for many years; things like default deny, network isolation, least privilege, inventory management, etc. Despite the good things about ZTA, its inclusion in the EO is premature and almost impractical.

ZTA is VERY difficult to implement in large, complex environments. We swear it’s easier and more effective to start over in some/most cases. Here are just some of the challenges with mandating ZTA wholesale like this EO appears to:
- Most people don’t know what a Zero Trust Architecture is.
- We already have a talent shortage problem (allegedly), this is going to take many knowledgeable people to implement.
- ZTA adds complexity, adding a Policy Engine (PE), a Policy Administrator (PA), Policy Enforcement Points (PEP), a Continuous Diagnostics and Mitigation (CDM) system, an industry compliance system, and (a lot) more.
- Deciding which variation of ZTA is the right one is no trivial task. There’s ZTA using enhanced identity governance, ZTA using micro-segmentation, ZTA using network infrastructure and software defined perimeters, device agent/gateway-based deployments, enclave deployments, resource portal-based deployments, device application sandboxing, and various combinations in between. If that’s not enough, there’s variations in trust algorithms too.
- From NIST SP 800-207, “Gaps that Prevent Immediate Move to ZTA”:
- Lack of Common Terms for ZTA Design, Planning, and Procurement
- Perception that ZTA Conflicts with Existing Federal Cybersecurity Policies
- From NIST SP 800-207, “Systemic Gaps that Impact ZTA”:
- Standardization of Interfaces Between Components
- Emerging Standards that Address Overreliance on Proprietary APIs
- From NIST SP 800-207, “Knowledge Gaps in ZTA and Future Areas of Research”:
- Attacker Response to ZTA
- User Experience in a ZTA Environment
- Resilience of ZTA to Enterprise and Network Disruption
- And many, many, many other challenges.
We can’t help but wonder if FCEB agencies and the Federal Government are ready for ZTA? Judging from last year’s FITARA scorecard (See: Figure 1 above), there’s still plenty of work to do on the fundamentals.
Let’s give the benefit of the doubt and just go for it, right? Here’s what we must do to get ZTA going in the Federal Government…
After preparing for the long arduous ZTA journey, step one in the migration “requires an organization to have detailed knowledge of its assets (physical and virtual), subjects (including user privileges), and business processes”. ZTA or not, every organization should have detailed knowledge of their assets.
NIST Special Publication 800-207, “Zero Trust Architecture”
How can you possibly protect the things you don’t know you have?
Start with an inventory of every single piece of hardware (firewalls, routers, switches, server chassis, workstations, laptops, mobile devices, and all other), then an inventory of every single piece of software (operating systems, client/server applications, cloud systems/applications, host applications, databases, and all other), then figure out your where your data is and where it goes (data flows).
Got it? OK, now map your business processes. If you’ve got all that figured out, you might want to consider throwing half of it away. You probably don’t “need” some of it, or you aren’t using it correctly anyway.
Step two, risk assessment and policy development. Step three is deployment, four is operations, then cycle back through continuously.
Vendors LOVE ZTA because it sells things, lots of things. The market is flooded with vendors who claim to sell ZTA solutions, but most of them are not ZTA solutions and most buyers won’t know the difference. Other vendors love ZTA because you’ll probably need software to do some/all of this. At a minimum, you’ll need a public key infrastructure (PKI), ID management system, and a security information and event management (SIEM) system.
All this adds more complexity to the environment, and complexity is the worst enemy of security. We sincerely hope ZTA isn’t in the EO for marketing to increase vendor sales (for companies with close ties).
Movement to secure cloud services
Certainly, cloud service providers like Microsoft, Amazon and others love seeing this in the EO. Sure, there are security benefits in using cloud services, but there are also drawbacks. It all comes down to “how” you use as much (or more than) “what” you use. In our opinion about ZTA (above), we mentioned that you cannot secure the things you don’t know you have. The follow-up is you can’t secure things you can’t control. When you move to the cloud, it’s not that you lose control, it’s that you have less control.
There’s also a concern that you’re giving attackers one (or a few) big juicy target(s) versus distributed ones. So, why accelerate movement to the cloud for better security? We’ll keep the rest of our thoughts to ourselves right now. This doesn’t sit 100% well with us.
Section 4. Enhancing Software Supply Chain Security – Summary
This section of the EO covers topics and requirements to:
- Develop standards, tools, and best practices for secure software development.
- Enforce secure software development practices.
- Define and enforce a “Software Bill of Materials (SBOM)”.
- Define “critical software” and its protection requirements.
- Consumer labeling programs for IoT and software.
This section contains two new topics and concepts that we haven’t seen before; the Software Bill of Materials (SBOM) and the consumer labeling programs.
Section 4. Enhancing Software Supply Chain Security – Opinion
If the requirements in this section are developed and implemented well, they could be great for information security. One of our concerns is (and has been) the insecure methods software developers follow and how we allow this to persist. Secure software development requirements and the transparency mentioned in this section of the EO is very intriguing.
We think the SBOM is a double-edged sword. On one side, it allows consumers (the government, organizations, people, etc.) to know where software comes from, how it’s made, and how to secure it better. On the flip side, this could be great intel for an adversary to build a better attack. We’ll have to see how this fleshes out.
Consumer labeling for IoT devices and software (and hardware) is too long in coming. Granted, many people won’t read the labeling, but for those who do, this is a great move.
All-in-all, there’s a lot of good stuff in this section of the EO. Let’s hope it all gets implemented well.
Section 5. Establishing a Cyber Safety Review Board – Summary
This section outlines requirements for a new “Cyber Safety Review Board”. All the requirements in this section are for the Secretary of Homeland Security and the (yet to be established) Cyber Safety Review Board (“board”).
This section contains high-level information about the board, when the board is convened, how the board is convened, who’s on the board, and what the board needs to do. Most of the responsibilities for the board are related to “cyber incidents”. The board reports directly to the Director of Homeland Security and by proxy, the President.
Section 5. Establishing a Cyber Safety Review Board – Opinion
There’s not enough detail to know what the board will do exactly. There is no charter or other detail provided; however, one of the board’s responsibilities is to create a charter. There is mention of membership, which we thought was interesting:
- Federal officials.
- Representatives of the Department of Defense
- Representatives of the Department of Justice
- Representatives of CISA
- Representatives of the NSA
- Representatives of the FBI
- Representatives from private-sector entities and/or “appropriate” private-sector cybersecurity or software suppliers as determined by the Secretary of Homeland Security.
Seems like the right government agencies are represented. We’ll have to see what the “appropriate” private-sector members will be. Let’s hope there’s no pay to play here!
Section 6. Standardizing the Federal Government’s Playbook for Responding to Cybersecurity
Vulnerabilities and Incidents – Summary
This section is about the creation of a standard set of cybersecurity and incident response procedures (or “playbook”).
The playbook:
- Will Incorporate all appropriate NIST standards.
- Be used by all Federal Civilian Executive Branch (FCEB) Agencies.
- Will articulate progress and completion through all phases of an incident response.
- Will allow flexibility so it may be used in support of various response activities.
- Establishes a requirement that the Director of CISA reviews and validates FCEB Agencies’ incident response and remediation results upon an agency’s completion of its incident response.
- Defines key terms and use such terms consistently with any statutory definitions.
Essentially, one “cyber incident” response plan to rule them all.
Section 6. Standardizing the Federal Government’s Playbook for Responding to Cybersecurity
Vulnerabilities and Incidents – Opinion
Getting all the FCEB Agencies to work from the same (or similar) playbook seems like a step in the right direction. The government will need to be careful that the playbook is kept confidential if/when it outlines details (which it likely will).
We’re sort of disappointed such a thing didn’t already exist. By the way, are we still sure we’re ready for ZTA?
Section 7. Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal
Government Networks – Summary
This section puts a lot of power in the hands of the Department of Homeland Security and the Cybersecurity and Infrastructure Security Agency (CISA).
Major topics covered in this section of the EO include:
- The adoption of a Federal Government-wide Endpoint Detection and Response (EDR) initiative.
- CISA threat hunting on FCEB networks and systems without agency authorization.
- Information sharing between the Department of Defense and the Department of Homeland Security
The timeline is aggressive, with EDR requirements mandated to be issued no later than September 9th, 2021.
Section 7. Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal
Government Networks – Opinion
We’re not against EDR as much as we are against adding more complexity to technology environments, especially when the environment is likely to contain tools that are not used well as it is. Adding more tools to an environment that already uses tools poorly just adds to the insanity.
Maybe the agencies are ready for EDR, but it’s hard to ignore that there’s going to be a HUGE payday for one or more vendors here. Which vendor or vendors? We’ll have to wait and see. Obviously, EDR only does what EDR does and there are some clear differentiators amongst the players in the market.
CISA doing threat hunting on FCEB networks without prior agency authorization should be interesting to watch. There need to be strict rules of engagement and strong oversight for such things. CISA will obviously need to hire many, many new employees, between this and all the other EO requirements. These will be employees that won’t be available to the private sector.
Section 8. Improving the Federal Government’s Investigative and Remediation Capabilities – Summary
The section of the EO is all about network logging, system logging and information sharing requirements.
FCEB Agencies and IT service providers will need to comply with (details TBD) requirements for logging events and retaining other relevant data within an agency’s systems and networks, including:
- Types of logs to be maintained.
- Time periods to retain the logs and other relevant data.
- Time periods for agencies to enable recommended logging and security requirements.
- How to protect logs (logs shall be protected by cryptographic methods to ensure integrity once collected and periodically verified against the hashes throughout their retention)
- Data shall be retained in a manner consistent with all applicable privacy laws and regulations.
- Ensure that, upon request, agencies provide logs to the Secretary of Homeland Security through the Director of CISA and to the FBI, consistent with applicable law.
- Permit agencies to share log information, as needed and appropriate, with other Federal agencies for cyber risks or incidents.
Once the requirements are set, enforcement will follow.
Section 8. Improving the Federal Government’s Investigative and Remediation Capabilities – Opinion
Standardized logging is a good thing, and it too has been a best practice for years. There are numerous sources for good logging configuration guidance, most notably being CIS and the STIGs. It’s important to point out that logs can (and often do) contain sensitive information. Sharing log files and other data can certainly help expedite and improve the quality of an incident response, but they can also be used by attackers to enhance the effectiveness of their attacks.
Share, but don’t.
Section 9. National Security Systems – Summary
Within 60 days, the Secretary of Defense must adopt National Security Systems requirements that are equivalent or exceed the requirements in the EO.
Section 9. National Security Systems – Opinion
This is a very short section and there isn’t much to comment on.
Section 10. Definitions – Summary
Eleven definitions are provided for words and/or terms used in the EO. There are useful definitions for “cyber incident”, “Federal Civilian Executive Branch Information Systems”, “Software Bill of Materials”, and “Zero Trust Architecture”.
Section 10. Definitions – Opinion
They are definitions and definitions are good for clarity. Interesting how the definition of “Zero Trust Architecture” is 227 words long. I like simple, so our simple definition is only two words long, “default deny”.
Section 11. General Provisions – Summary
Looks like some legal stuff. No information security requirements cited in this section.
Section 11. General Provisions – Opinion
No opinion on this section.
Conclusion
There’s plenty to unpack in this Executive Order. Most of the requirements in the EO were reasonable and should result in a net positive in terms of better cybersecurity protection. Requirements that are a little concerning are the Zero Trust Architecture (ZTA) requirements (which we think are premature), prioritized movement to cloud services (which we think could be unjustified from a security standpoint), quick adoption of an endpoint detection and response (EDR) initiative (adding more to manage to environments that are already complex), and unauthorized (by the FCEB Agency) threat hunting.
Other points to consider:
- Would this prevent or mitigate some of our current attacks? This is a longer discussion.
- The timeline is extremely aggressive.
- The requirements are very expensive.
- Those who benefit the most include the Federal Government itself, (big) cloud service providers, ZTA solution providers, and EDR software makers.
- Those who benefit less are private sector organizations, state and local governments, education (K12 and higher ed), small to mid-sized businesses, and people at home.
This EO is essentially law; therefore, like it or not, (our) compliance is mandatory.

A simple, objective, measurable, and scalable standard for accountable risk management in state government.
Introduction
The challenges facing information security (or “cybersecurity”) personnel in state government are endless. State Chief Information Security Officers (CISOs) are too often put in the unenviable position of trying to secure their state’s information assets without adequate support from their governor, legislators, agency heads, or the citizens they serve. The lack of support isn’t due to neglect or indifference, but due to the lack of effective communication, a fundamental understanding of information security risk, and accountability.
SecurityStudio works with state CISOs and governments to simplify information security risk management for optimal effectiveness, without taking shortcuts.
Every state is different
No two states among our fifty are the same.
Some states are more distributed than others. Some states have greater influence on county, city, and local municipal government than others. Some states govern education, both K12 and higher education, more closely than others. Although every state operates differently, information security fundamentals and logic are the same everywhere.
SecurityStudio engages with all states at various levels to make information security better for everyone.
The state of information security in the state
Without knowing where we are, how will we get where we need to go?
The question points to a common problem in state government, reinforced by a recent conversation between a state technology committee chair and our (SecurityStudio) team. The chair asked SecurityStudio to discuss cybersecurity concerns with the committee, but more specifically, the committee wanted to know what their state should do next with cybersecurity.
Chair: We’d like you to come to our next meeting and tell us what we should consider next and what other states are doing. What is our greatest cybersecurity concern today?
SecurityStudio: Good question. It’s fundamental. The state doesn’t know the current state of information security within the state. Furthermore, the state doesn’t know what the future state of information security should be, when it should get there, or how much it would cost.
Chair: What do you mean?
SecurityStudio: Let me ask you this question, do you know the current state of information security within the state?
Chair: No, not really. We’ve seen various reports, but nothing that indicates an objective view of information security across all of state government.
SecurityStudio: Nobody can determine a future state or make good risk decisions without defining where things sit today. The state needs to adopt a simple, objective, measurable, and scalable standard for accountable risk management, read more on the 4 steps here.
Without a current state, how will the state know if its spending on the right things, whether it’s getting an adequate return (in the form of reduced risk) or if it’s effecting proper accountability. We need to be more accountable to the citizens we serve.
Chair: Today, we justify how well we’re doing by how much money we spend on cybersecurity.
SecurityStudio: This is the wrong metric. $10M spent on ineffective or the wrong information security controls can be worse than spending no money at all. Information security budgets must be justified by risk, not by opinion or the latest trend.
We need to help our governor, legislators, CIO and CISO obtain better visibility into information security risk and provide objective justifications for our spending.
Chair: The state is a big, complex organization. How would we get our hands around it all?
SecurityStudio: We start simple and keep it simple, all without compromising quality or accuracy. There are seven simple steps:
- Obtain or create an inventory of administrative, physical, and technical components (or “entities”) that complete our state’s government.
- Define accountability for each entity.
- Perform simple, effective, and consistent risk assessments of each entity.
- Using the standard definition of information security.
- Using objective (binary) criteria.
- With consistent, logical measurement and sensical scoring.
- Compile and communicate results with the governor and legislature.
- Make risk decisions (using measurement as our guide).
- Plan and budget, creating the state’s roadmap.
- Implement changes and measure progress.
We built an affordable software platform to manage and automate everything that can be automated. We can show you a demonstration during the committee meeting.
Chair: Excellent! This will be a great discussion. I’m excited to see what you’ll show us.
Most states have the same (or a similar) issues as those described in this real conversation.
How SecurityStudio helps with this problem
SecurityStudio was built specifically for fundamental information security challenges facing state CISOs.

The primary risk management tool on the SecurityStudio (or S2) platform is the SecurityStudio Organizational Risk Management Tool (or S2Org). For the current state of information security in a state to be accurate, the “state” or risk assessment score (S2Score) must represent risk across all state branches and agencies; however, it’s often necessary to go further.
Some states provide shared infrastructure and/or services to counties, cities, other municipalities, K12 education, and/or higher education. In shared resource cases, states leverage the many benefits of S2Org’s built-in “nested entities” function. The two most valuable benefits for states and state CISOs are:
- Accuracy. The most accurate representation of risk through measurements and answers provided by personnel who are best suited to provide them.
- Accountability. Distributed accountability for an entity (or portion of an entity) to responsible personnel for assessment and/or remediation with a few clicks.
Additional tools on the S2 platform used by state and local governments include 2Team and 2Me. 2Me is a free personal information security risk management tool for everyone. The State of North Dakota was the first state to make 2Me available to all their citizens through an ongoing awareness campaign called #BECYBERSMART. 2Me is available to all states as a white labeled option at no cost.

2Team is used by employers (including the state itself and its sub-entities) to learn about employee information security habits at home, using data from 2Me. ONLY anonymous and aggregated data is shared with employers through the 2Team portal; however, the data can still be invaluable for helping employees secure themselves and/or their families better.

Conclusion
Understanding and managing “the state of information security in the state” is NOW attainable for governors, legislators, agency heads, CIOs, CISOs, and our citizens who rely upon us to do our best.
From the current state:
- The future state can be determined,
- The time to reach the future state can be defined, and,
- Cost (budget) can be justified and our spend can be quantified.
Information security management for state and local government cannot be made any simpler, more objective, more measurable, more scalable, more standardized, or more accountable than we’ve made it with SecurityStudio!
Before we close, we’re also affordable, leaving you with more money for remediation.
Contact SecurityStudio
We are always here to serve.
- To schedule a demonstration of the SecurityStudio platform or to arrange a trial, contact Evan Francen at efrancen@stg-securitystudio-staging.kinsta.cloud.
- To learn more about SecurityStudio, our tools, or our #MissionBeforeMoney, visit us online at https://securitystudio.com

Introduction
Before we dig in, let’s clarify “Vendor Risk Management”. The title of this article isn’t entirely accurate. The term “vendor risk management” and “vendor information security risk management” are two different things, but our industry often uses them interchangeably.
Vendor risk management (or “VRM” for short) rolls off the tongue better, ranks better in search results, and sells more products, but vendor information security risk management (or “VISRM” for short) is more accurate when discussing information security risk versus business risk. You might not be aware of the differences:
- Vendor risk management deals with business risk. Business risk includes financial risk, reputational risk, business process risk, legal risk, information security risk, and every other risk that a business deals with related to a vendor relationship.
- Vendor information security risk management deals with information security risk related to the vendor relationship. Information security risk is part of business risk, but it is not business risk.
The words “vendor”, “third-party”, and “supplier” are essentially the same, or close enough. Our preference is third-party because it accounts for vendors (people who sell things), suppliers (people who supply things), and all others third parties we might share data with.
Clarity in knowing that VISRM is part of a greater VRM program is important as you design and mature your approach to these things.
What is Vendor information security risk management?

It helps to break things down. A vendor is any person or organization who provides goods and/or services for a fee. Information security risk management (the “ISRM” part of the equation) requires more clarification. To “manage” information security risk, we simply ensure these three steps are followed:
- Assess – use a simple, objective, and measurable information security risk assessment. Information security must account for risks related to:
- People
- Physical (controls)
- Technical (controls)
- Decide – Only four choices; accept (as-is), mitigate, transfer, or avoid.
- Implement – implement or do what the risk decision is/was.
Now that we’re on the same page about what vendor information security risk management is, here are the nine things we must do if we want to do it right!
#1 – Define why.
It’s common for people and organizations to rush into something without a clear understanding of why they’re doing it. Even if someone within an organization knows why, do the others? Don’t assume that everyone knows, especially the business stakeholders who will ultimately determine whether we’re successful or not. Questions we must have good answers for:
- Why are we doing Vendor Information Risk Management?
- What’s the purpose of our VISRM program?
- What will determine success in our Vendor information security risk management program?
Aimless VISRM programs are a waste of money and are frustrating to manage. Vendors who pose significant risk to the organization will be allowed to operate as-is if we don’t have the support of business leaders, and we only get support with a well-defined “why?”
Try this, “We are doing VISRM because:
- we need to meet our (insert regulation here) compliance requirements.”
- (insert competitor name here) is doing it.”
- we don’t want to be found liable for a vendor-related data breach.”
- we want to be defensible by demonstrating proper due diligence in managing vendor risk.”
- vendor relationships pose a significant risk, and we must account for the risk in our overall information security risk management program.”
Pick your reason, document it (maybe in a policy or charter) and stick to it in every VISRM thing you do.
#2 – Get buy-in.
Without business buy-in, we’ll be going through the motions at best and getting fired at worst. The best VISRM programs are championed from the top. Take the documented reason for VISRM (from above) and get executive management’s opinion. Refine statements and documentation if necessary and seek their support (not just approval). Without their support, we’re fighting an uphill battle, and it won’t turn out well.
When the business is bought in, good risk decisions can be made, and vendors can be held accountable for remediation (or face termination of the relationship). We won’t be able to push back on vendors without management/business support, and our vendors know it.
#3 – Sooner is better.
VISRM processes must be integrated early into procurement processes while information security risk decisions can still be made. If VISRM is the last or a late step in the procurement process, it may be too late to do anything about risk. If the business has already made necessary accommodations and adjustments for the purchase of the vendor’s goods and/or services, we’ll find it more difficult to conduct a proper risk assessment, and nearly impossible to get the vendor to perform any significant risk remediation.
We’re certain to accept more risk than originally intended and have more vendor relationship risk exceptions when we insert VISRM late into procurement processes.
#4 – Share the work.
VISRM is not a single person’s or team’s responsibility. VISRM is a shared responsibility between the business and information security (or risk) personnel.
Roles and responsibilities for VISRM must be defined, documented, and communicated. It’s common for an organization to assign all VISRM responsibilities to a single person, and this is a poor practice. A single person will not know how every vendor is used or who every vendor contact is.
Applying the concept of relationship manager and risk manager is a good approach. The person, or team within the organization who uses the vendor’s goods or services is the relationship manager and should be the person who completes the classification of the vendor relationship (see #5 below). The person, or team, within the organization who handles the VISRM process is the risk manager.
Distributing the work between relationship managers and risk managers makes the VISRM a collaborative effort between the business and information security (or risk) personnel. It also makes things more accurate and efficient.
#5 – Relationships are unique.
Two types of risk that are important to remember, inherent risk and residual risk.
- Inherent risk – risk associated with something (a vendor relationship) without accounting for controls to address risk.
- Residual risk – risk associated with something (a vendor relationship) after accounting for controls to address risk.
Inherent risk (called “impact” in some tools) is used to classify the vendor relationship based on how the vendor is used, usually as “High”, “Medium”, or “Low”. A vendor with access to thousands of sensitive or confidential records poses a higher inherent risk than a vendor who has no access to data (a toilet paper supplier for instance).
It’s inefficient and senseless to treat all vendors the same, a waste of time and resources.
#6 – Keep it simple.
Complexity is the worst enemy of information security. Simplify, but don’t oversimplify. There are only four steps, no more and no less:
- Inventory – an accounting of vendor relationships is critical because we can’t possibly secure things we don’t know about. Compiling an inventory for the first time will require some work, and the best place to start is probably the accounting (accounts payable) department. Vendors are paid through invoices, reimbursements, and/or corporate card payments. Once the inventory is compiled, we’ll need to make sure it stays current. This is where we’ll need to insert VISRM into the organization’s procurement processes.
- Classification – Keep this simple. Think of ten or fewer questions we could ask to classify a vendor relationship as “High”, “Medium”, or “Low” based on inherent risk. These should be questions that a vendor relationship manager can answer.
- Assessment – Higher inherent risk relationships need to be assessed for residual risk (see above). Low inherent risk relationships can probably be ignored while we focus on “High” and “Medium” vendors. The most common method of assessment is a questionnaire.
- Decision-Making – When we have a risk, we only have four options:
- Accept – risk is acceptable as-is.
- Mitigate – risk is unacceptable, and the vendor needs to implement a control or change one.
- Transfer – hand risk to someone else, usually through insurance and/or contractual language.
- Avoid – risk is unacceptable, and remediation isn’t an option; therefore, the relationship will be terminated.
If our VISRM program doesn’t include these four steps, or includes more than these four steps, we’re probably not doing it right.
#7 – Manage requires measure.
“You can’t manage what you can’t measure.”
Measurements are important for comparison, context, trending, and objectivity.
For example, let’s say we score vendor relationship risk on a scale of 300 (high risk) to 850 (no risk). If scoring is consistently applied within the assessment and between assessments, we can compare risks with each other, we can track risk over time, and we could set objective thresholds for acceptable versus unacceptable risk.
VISRM without measurement is less effective and less defensible.
#8 – Automate without shortcuts.
Automate everything we can without taking shortcuts. The “IS” in VISRM stands for “information security” and information security must account for administrative, physical, and technical controls (and risks). The most common shortcut is to treat information security as an IT or technical issue rather than a holistic business issue.
Think about it. Isn’t it easier to go through the secretary than the firewall, and who cares about the antivirus software running on a server when someone steals the server?
Information security is NOT an IT issue, it IS a business issue.
#9 – Progress over perfection.
VISRM can seem daunting, and it’s impossible if the pursuit is perfection.
The goal is progress, and progress is defensible. Start with building the initial vendor inventory. Next, implement processes to ensure the inventory stays current, meaning integration with procurement process(es). Getting here could take a year in some organizations. Fine. It’s progress.
Set attainable risk management goals. Let’s say we have 1,000 vendor relationships. Maybe an appropriate goal for a twelve-month period is to classify all vendor relationships and conduct a dozen or so “High” risk assessments (step #3 from above). Again, more progress.
Then continue down the path. This is a maturation process and a journey, not a magic process and a teleportation.
Conclusion
The case for VISRM is indisputable, given the facts and regardless of what motivates.
- Driven by risk – according to some studies as much as 60% of all data breaches come through a vendor relationship, directly or indirectly. The impact ranges from thousands or millions of dollars to bankruptcy.
- Driven by compliance – most industry regulations require VISRM, including HIPAA, GLBA, and others.
- Driven by legal liability – the absence of a VISRM program makes the organization less legally defensible in a civil action (resulting from a data breach).
Ignorance will not protect the organization. The most common risks from vendor relationships are data loss, ransomware (or other malware), and network entry through remote access (VPN, RDP, etc.).
The cost of a good VISRM tool like S2Vendor, provided by SecurityStudio, can be a little as $200/month. You can choose to do VISRM now or be forced to do it later. From experience, I can tell you doing it now is a lot less painful.

What is Threat Monitoring
SecurityStudio recently announced adding a new feature to S2Me and S2Team called “Threat Monitoring”. It’s wrong to assume that everyone knows what threat monitoring is, so we put together a short article to explain. A threat, and the definition of “threat”, is best understood when they are put into context, and this is where we’ll start.
S2Me and S2Team are both risk management tools. S2Me is for personal risk management and S2Team is for employee personal risk management.
The key to managing risk is understanding risk.
The understanding of “risk” is critical to understanding the concept of information security, privacy, and personal safety. The meaning of risk is also very important to the meaning of threat(s) because they’re interrelated.
Risk is the likelihood of something bad happening combined with the impact of something bad happening.
The “something bad happening” is derived from threats and vulnerabilities. A threat is “a person or thing likely to cause damage or danger” and a vulnerability is a weakness (in protection). Threats, when applied to vulnerabilities, result in risks.
Do you see the relationship? It might be a little clearer when we substitute “something bad happening” in our risk definition. When we do, the definition of risk looks like this:
Risk is the likelihood of a (threat acting upon a vulnerability) combined with the impact of the (threat acting upon a vulnerability). Risks are difficult to predict, but there are many examples:
- The risk of a compromised bank account.
- The risk of ransomware.
- The risk of lost personal information.
- The risk of lost privacy.
The number of risks we face each day can be great, depending on many factors.
SecurityStudio’s threat monitoring is our method of monitoring threats (“person or thing”) that are likely to cause you damage or danger.
How SecurityStudio’s Threat Monitoring Works
Threat monitoring is an evolving science. Threats are always evolving, techniques to discover threats are always evolving, and SecurityStudio’s solutions are always evolving too.
This first version of our threat monitoring solution is simple and focused. We’re identifying data breaches and incidents where your account or personally identifiable information may have been compromised, then notifying you to take some action in response. We follow a simple four-step process:
- Discovery – SecurityStudio systems are constantly scouring multiple reputable online sources for data breach and incident-related information.
- Collection – We collect all the breach and incident information we find, compile it, and store it in our own localized data warehouse.
- Identification – Multiple times a day, we mine our data warehouse, searching for indicators of compromise related to you (and all other S2Me subscribers).
- Notification – If indicators of compromise related to you are discovered, we notify you immediately by email (if you’ve got the feature turned on) and post the information into your secure S2Me portal.

Display of Threat Monitoring in the S2Me Portal.
For S2Team, the same process is followed with one additional step: compilation of the information in the organization’s management dashboard for ease of management and response.

Display of Threat Monitoring in S2Team.
Everyone (but the bad guys) Benefits from Threat Monitoring
Everyone, except for members of remote tribes, has a digital identity. With a digital identity comes opportunity for an attacker to profit and risk for you to lose something of value. This applies to business leaders, employees, grandparents, parents, kids, and everything in between.
S2Me Threat Monitoring is just one solution you should consider. There is no single source of all threat information.
Benefits for S2Me subscribers:
- Your digital identity is monitored constantly, so you can rest a little easier knowing that SecurityStudio’s team of cybersecurity experts is keeping an eye out for you.
- The data we compile is data you can trust; it comes from reputable sources and it’s validated before it ever reaches your inbox or portal.
- Your identity information is mathematically validated, reducing the chances of false alerts and cluttered inboxes.
- S2Me is free and always will be. There’s no catch, and you won’t be sold something you don’t need.
- Checklists keep track of whether you’ve read the threat information, and whether you’ve responded appropriately to the threat.
Benefits for S2Team subscribers:
Employees enjoy all the S2Me benefits (above), in addition to having trusted advisors (the organization’s information security team) to help, and the confidence in knowing nobody else sees their individual S2Me results.
Employers benefit from S2Team by:
- Knowing which employee accounts may have been compromised quickly enough to respond before damage is done.
- Receiving immediate notifications of relevant data breaches and incidents.
- Being able to use relevant data breach and incident information in more effective information security awareness and education campaigns.
- Fostering a closer partnership with the organization’s user community by showing goodwill and care about employee personal protection (at home including family).
When You’re Notified of a New Threat
Don’t panic. You received a threat notification because we detected your personal information was probably involved in a data breach or incident, but NOT that your personal information was used (yet). In most cases, you have time to respond before damage is done.
The first step is to log into your S2Me account and go to the Threat Monitoring tab.

Here you will find all the data breaches and incidents we know about that concern you. Listed at the top will be the data breach or incident you were most recently notified about, along with additional information. In the example below, we may have received a notification about a data breach related to “Wattpad”.

A short description of the incident is provided along with the data that was compromised and your checklist of actions you should take. The two most common suggested actions are to “Read” the information (and check off that you have) and to change your password (checking off “Password Changed” when you have).
That may be all you need to do, especially if you’re following the other guidance provided in the S2Me personal information security risk assessment.
Do This Now
If you haven’t subscribed to SecurityStudio’s S2Me, do it now. S2Me is the standard personal information security risk management tool used by thousands of people across the globe, and it’s the only tool endorsed by state and local governments in the U.S. The free S2Me guides subscribers through a simple information security risk assessment across ten important topics:
- Household Desktop and Laptop Use
- Safe Practices for Internet Usage
- Choosing and Protecting Authentication
- Securing Mobile Devices
- Securing WiFi
- Secure Gateway
- Backing up Data
- Internet-of-Things (IoT) and Other Devices
- Physical Security
- Breach and Incident Response
A completed assessment results in your personal S2Score for tracking your progress as you follow recommendations and build better information security habits.

By default, Threat Monitoring will be turned on when you create your S2Me account and you’ll enjoy all the benefits.
For Employers
Subscribe to SecurityStudio’s S2Team and deploy S2Me to all your employees and customers. Encouraging employees to protect themselves better at home is a welcome opportunity to foster information security collaboration by showing you care. The insights you gain into employee information security habits will become invaluable as you partner to make information security better for everyone.
There’s no better way to secure the remote workplace than by motivating employees to secure their homes and families better.
Loyal customers expect loyalty in return. Organizations, in growing numbers, are providing S2Me to customers and encouraging their customers to protect themselves better. The organization benefits by demonstrating loyalty, and depending upon the type of business, reduced loss.
The Future of S2Me and S2Team Threat Monitoring
This is just the beginning of what SecurityStudio has in mind to improve information security and threat monitoring for everyday people. This first version of Threat Monitoring uses technology and techniques that have been in the marketplace for a while, but now that we’ve establish a solid base to work from, we can truly innovate!
Ideas include:
- Improving our current threat monitoring model to correlate detected attacker activities beyond the original incident.
- Monitoring threats related to physical location.
- Monitoring threats related to social media account usage and security.
- Monitoring threats related to specific systems and devices in use.
- Integration with other live Internet activity feeds for more relevance and focus.
Stay connected to SecurityStudio to learn about our latest news!
At SecurityStudio, we are 100% committed to our mission. Our mission is to fix the broken information security industry by focusing our efforts first on where they’re most needed. Our mission always comes first. #MissionBeforeMoney

Cybersecurity has never been more important than it is today. Not only is our information more at risk, but so is our privacy, and even our personal safety. Complexity and distraction have contributed to us “taking our eye” off the ball, and there’s no better time than now to act.
What is cybersecurity?
This is a confusing word for some people. Even cybersecurity experts have different explanations of what cybersecurity is.
Cybersecurity is Managing the risk of unauthorized disclosure, modification, and destruction of information through technical means.
The key is managing risk, not eliminating risk. Eliminating risk would require us to eliminate all our information and the electronics we leverage to create, transfer, access, and use it. No more laptops, no iPads, no mobile devices, no Internet, and no data. Obviously, this isn’t feasible, and neither is eliminating risk.
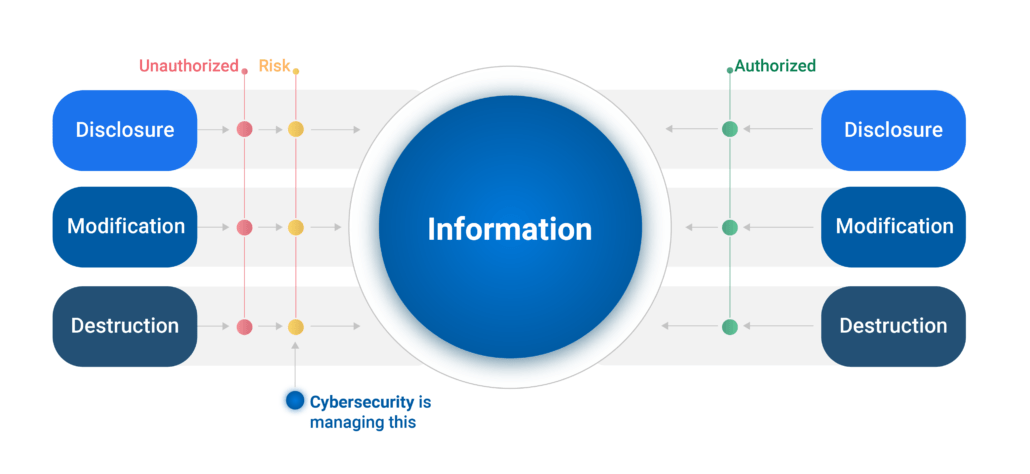
Managing risk means we need to live with the fact that bad things can and will happen; therefore, detecting bad things early and having a prudent response are also important.
Why is cybersecurity more important than ever?
The simple answer is bad things are happening more often and the results are more impactful. We were riding a dangerous trend of increased incidents (ransomware, data breaches, etc.) prior to 2020:
- Over the past 10 years, there were 300 data breaches involving the theft of 100,000 or more records.
- There were 1,244 data breaches in 2018 and 446.5 million records were exposed.
- There were 4.1 billion records exposed in the first six months of 2019 alone.
- At the beginning of 2019, the World Economic Forum named cyber-attacks as one of the top five risks to global stability.
2020 has certainly been a year like no other, and things haven’t gotten better. The final numbers aren’t in for this year’s cybersecurity incidents, but we inherently know things have gotten worse. There are two primary reasons for higher risk in 2020; complexity and distraction.
Complexity is the greatest enemy of cybersecurity. Most business and home technology environments have gotten too complex to secure properly. Businesses and people struggle to know what things they’re securing, let alone how to secure them. At home the problem is getting worse with each new technology we add. In our lust for new technology and features, we’ve failed to slow down and think about the cybersecurity consequences of our choices. Technology complexity continues to explode with “smart” homes (Alexa, Google Home, Ring, etc.), “smart” cars, interconnected medical devices, and our 275 million “smart” phones.
In terms of impact, our lives have become so interconnected that we can no longer separate cybersecurity from privacy or physical safety.
2020 has been a debacle. We’ve never been more distracted. There are so many significant things going on, that many of us have taken our eye off the cybersecurity ball. COVID-19 flipped our world on its head. Offices closed, leading to an explosion of work-from-home. Schools closed, leading to an explosion in remote learning. Couple these events with health concerns, economic concerns, general uncertainty, and it’s understandable that cybersecurity becomes an afterthought.
If COVID-19 wasn’t a significant enough distraction, 2020 also brought real social justice issues, civil unrest, the presidential election, and disinformation campaigns that bombard our inboxes and social media feeds.
Complexity and life’s distractions in 2020 have made our digital lives a perfect attacker’s playground.
Why are cybercrimes on the rise? How did they evolve over time?
Cybercrimes are on the rise because the opportunities we give attackers are extensive and the return on the attacker’s investment has never been higher. It’s the perfect recipe for their success at our expense.
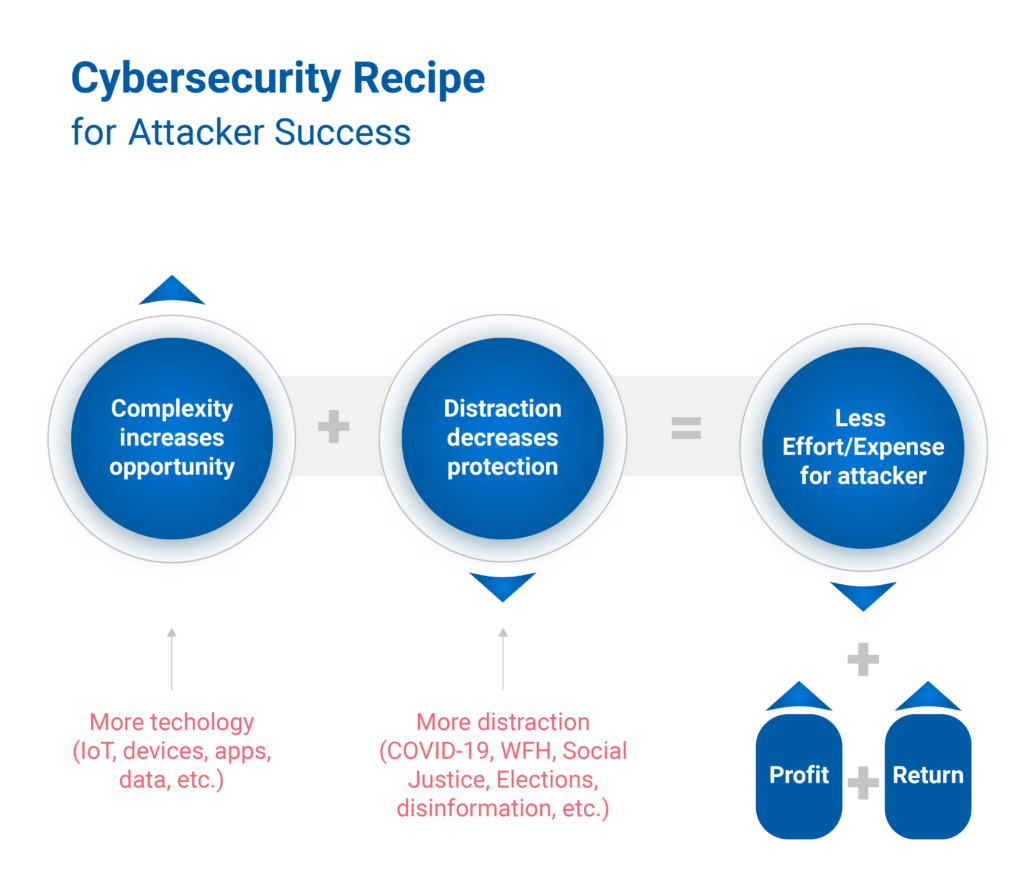
We continue to increase opportunities for attackers through our incessant need for more technology, while at the same time, we’re distracted by life’s events. These things combine to make attacks easier and more successful, leading to increased profit and return for an attacker. The cycle repeats itself when attackers re-invest their profits into better and more frequent attacks.
In previous decades, attacks were less nefarious, and it wasn’t uncommon for an attacker to be motivated by bragging rights or showing off. Those days are long gone, and criminals are organized much like legitimate businesses. Businesses are in business to make money, and so are most attackers. 71% of all data breaches are financially motivated and 25% are motivated by espionage.
The attackers we should all be most concerned about are the ones who are motivated by money and power; these are often organized crime rings and nation-state attackers such as China, Russia, and Iran.
What is the impact of a cybercrime to your organization, team, and/or self?
The impact of cybercrime depends upon several factors; the nature of the incident, your ability to detect and respond to the incident, the intent of the attacker, and the attacker’s ability or skill to carry out their intent. The impact can range from a simple nuisance to bankruptcy, and in rare cases even death.
For small to mid-sized organizations (250-449) employees, the downtime from a data breach varies:
- 43% reported 0-4 hours of downtime
- 45% reported 5-16 hours of downtime
- 12% reported 17-48 hours of downtime
Sadly, 56% of Americans don’t know what steps to take in the event of a data breach (including American businesses), an estimated 60% of small to mid-sized business fail within 12 months of experiencing a data breach, and in 2020 we read about the first (known) death related to ransomware.
The impact of cybercrime varies from low to severe. How low or how severe should not be left to chance because you can (and must) take steps to reduce your risk.
What can you do to protect your organization, your team, and yourself?
The most important thing for all of us is to understand and apply basic cybersecurity principles. The most basic principle starts with risk management. Cybersecurity is risk management. In order to manage risk, you and I must understand (assess) it. Find a good, fundamental risk assessment, and do it. You’ll need to assess risk personally (at home), in your third-party/vendor relationships (the people you share information with), and within your organization.
How can SecurityStudio help?
SecurityStudio is dedicated to our mission of fixing the broken cybersecurity industry by helping people with simple, inexpensive (even free), and effective information security risk management tools.
- Organization risk management starts with the S2Org tool, used by thousands of organizations of all sizes across all industries.
- Third-party/vendor risk management starts with our S2Vendor tool; integrated, organized, and automated (without taking shortcuts).
- Personal risk management (at home) starts with our S2Me tool; 100% free and simplified for everyday people.
- Work at home risk management starts with our S2Team tool; the most cost-effective insight into employees’ real information security habits.
If complexity is the worst enemy and if cybersecurity is risk management, then we all need simple and affordable risk management tools for everyone to build the best defense, detection, and response capabilities possible.
SecurityStudio is here to help, always dedicated to #MissionBeforeMoney.

